In the text payload, a section called UDH (User Data Header) is optional but defines lot of advanced features not all mobiles are compatible with. One of these options enables the user to change the reply address of the text. If the destination mobile is compatible with it, and if the receiver tries to answer to the text, he will not respond to the original number, but to the specified one. Most carriers don’t check this part of the message, which means one can write whatever he wants in this section : a special number like 911, or the number of somebody else.In this connection, the attacker does not recommend the sharing of important information via the iPhone SMS. Also you can try to fix sending SMS if have that problem too. Just use this iPhone SMS security app and you will find out out. In addition, users should not trust suspicious messages, even if they are sent from a familiar number, hacker says presenting Sendrawpdu. You can also read about another thread - iKee b. Worn and how to clean it from your iPhone 4 iOS. Prior to launching iOS 6 is only a few weeks. While the firmware is in beta testing, the developers have time to fix the vulnerability, thus protecting users from phishing attacks. I think that this is the first that Apple has to do. How do you think? Have you tried Sendrawpdu SMS security app?
Recent Blog

Ultimate Guide: How to turn Off Restricted Mode on iPhone?

Automate Apple GSX check result obtaining?

iRemove Unlock iPhone 5S, 5C, 5, SE, 4S/4 Software

MacOS High Sierra Features: Set Up Websites in Safari on Mac
How to Enable iOS 11 Mail Reply Notification on iPhone 7

How to Bypass Apple Watch Passcode Problem
LetsUnlock Services List
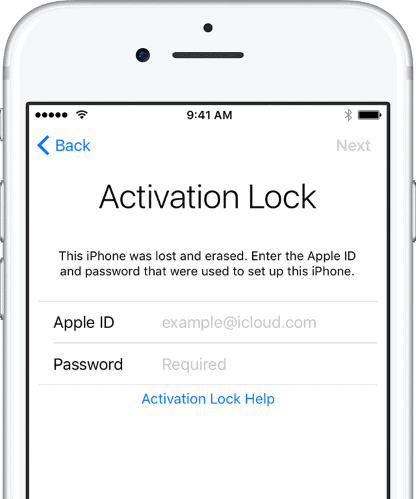
iPhone & iPad Activation Lock Bypass
Use LetsUnlock iCloud Tool to bypass Activation Lock Screen on iPhone and iPad running on iOS version up to 14.6.
Read More
Unlock Passcode Disabled iPhone or iPad
LetsUnlock iCloud Tool is ready to remove Find My and unlock your passcode disable device running on iOS 13.x.x in one click!
Read More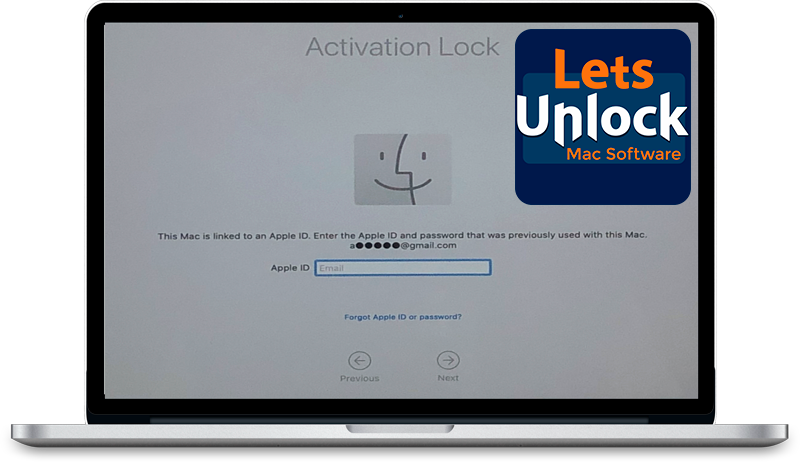
MacOS iCloud Activation Lock Bypass
The LetsUnlock Mac iCloud Activation Lock Bypass Tool will help you to remove Activation Lock on an iCloud locked Mac which is stuck on Activation Lock Screen with no need to enter the correct Apple ID and password.
Read More
Mac EFI Firmware Passcode Bypass
The LetsUnlock EFI Bypass Tool is a one button solution, which you click to start the EFI Unlock process. Bypass EFI with out password! Everything else does the software.
Read More
MacOS iCloud System PIN Bypass
The LetsUnlock MacOS iCloud System PIN Bypass Tool was designed to bypass iCloud PIN lock on macOS without passcode!
Read More