Ultimate Guide: How to turn Off Restricted Mode on iPhone?

Automate Apple GSX check result obtaining?

iRemove Unlock iPhone 5S, 5C, 5, SE, 4S/4 Software

MacOS High Sierra Features: Set Up Websites in Safari on Mac
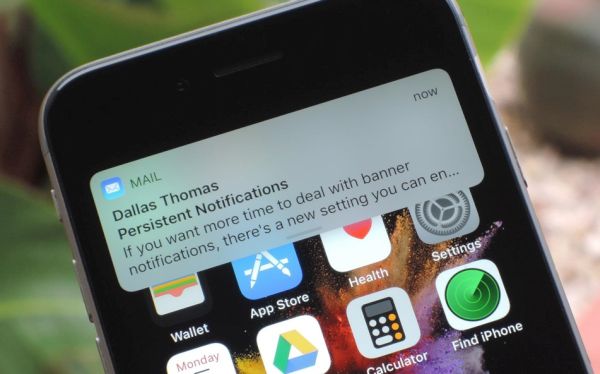
How to Enable iOS 11 Mail Reply Notification on iPhone 7

How to Bypass Apple Watch Passcode Problem

How to Restrict Safari Features on iOS 11: Camera Access and Microphone Use
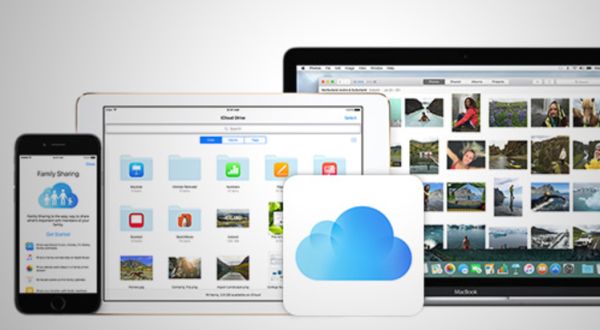
iOS 11 Family Sharing iCloud Storage Option on iPhone

How to Stop Safari from Tracking iOS 11 iPhone Web History
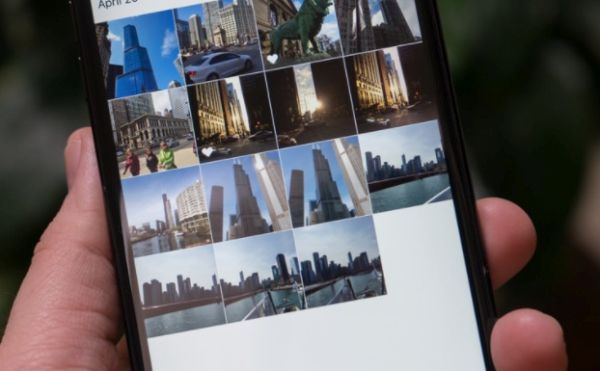
How to Rename iOS 11 Photo Album on Your iPhone

How to Use iPhone 8 Control Center on iOS 11 Without 3D Touch

How to Use iOS 11 Beta on iPad Pro: Drag and Drop Feature
Explore iOS 11: Learn to Save and View Gifs on iPhone 7 and iPad

iOS 11 Siri Translate Feature: How to Use This Translation on iPhone
How to Recover Deleted Files from iPhone on iOS 11
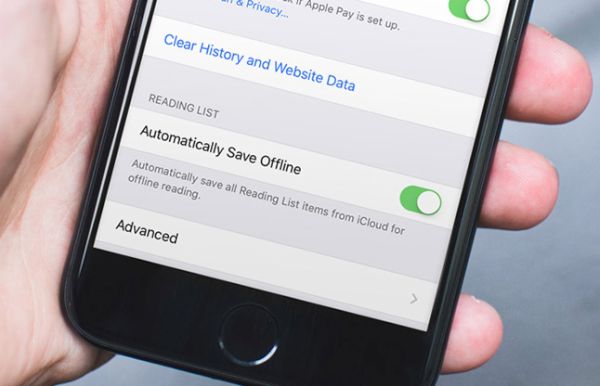
How to Save iOS 11 iPhone Reading List to iCloud Using Safari

Get iPhone Safari Update on Newest iOS 11 Beta 2 to See Awesome Features

How to bypass configuration profile on iOS

How to Maximize iPhone Battery Life on iOS 11 Software Version
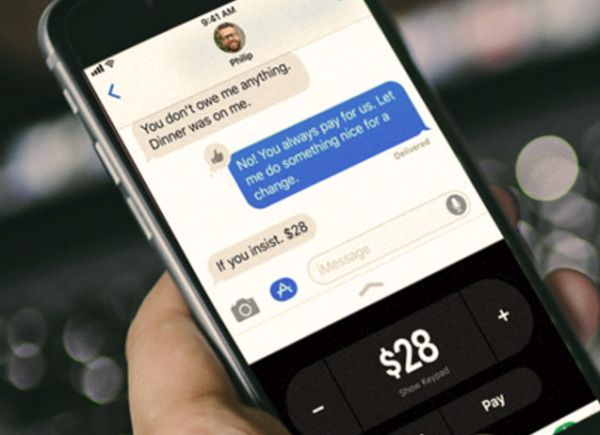
iPhone Users Can Send and Receive Cash via iMessage

How to Reboot Your iOS 11 iPhone: No Power Button Action
How to Remove Apps on iOS 11 Without Deleting Data on iPhone

How to Enjoy New iOS 11 Feature without Developer Account on iPhone or iPad
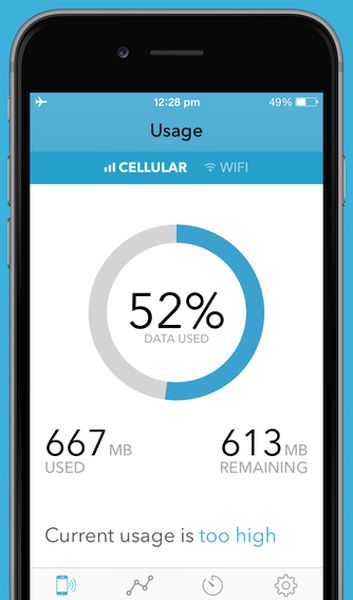
How to Check iOS 10 Mobile Data Usage on iPhone 6 and 7
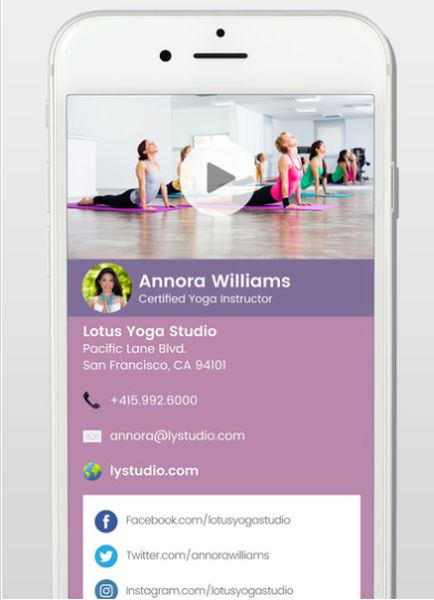
How to Make a Digital Business Card with Photos, Videos on iPhone

Your iPhone Keeps Restarting Itself? Fix This Boot Loop
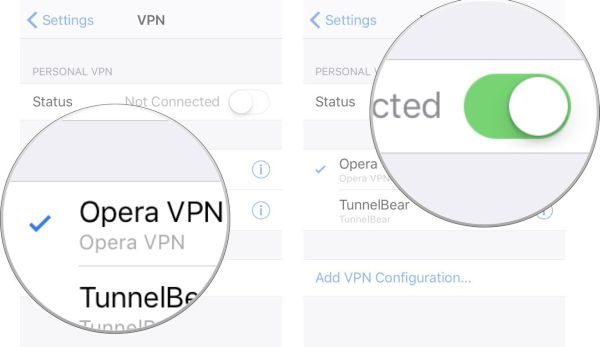
iPhone VPN App: How to Setup and Configure Settings

How to Install New Firmware on Your AirPods

iPhone 3D Touch Hidden Shortcut Feature: How to Use It
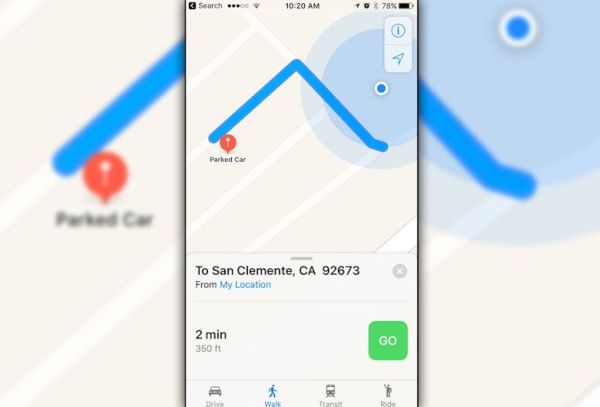
How to Remember Google Maps Parking Locations on iPhone
