- Ikee.a
- Ikee.b
- Ikee.c
- Ikee.d
Ikee.B Virus
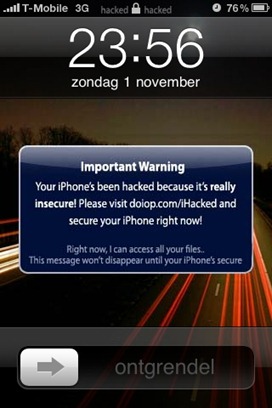
Here will be presented the analysis of Ikee.b virus that targeted iPhone users in Europe and Australia back in Novermber 2009. Just a short time after Ikee.a "party" the modified version of the virus started its action. Originally developed by a Dutch hacker it was uploaded by SSH to unsecured devices with default password. The hacker just scanned T-Mobile's Dutch IP range for those SSH-vulnerable devices and infected them. The devices got hacked and displayed such messages:The guy demanded $5 from the victim for making the device safe again. However, soon after the launch he got caught and forced to return the money to cheated owners.
The new Ikee.b malware was designed identically to Ikee.a but included one significant distinction - command and control (C&C) logic that helped to manage all the iPhones infected by a bot master. That actually turned infected iPhones into parts of a botnet. Besides the fact that Ikee.b bot has ability to self-propagate, it can introduce a C&C checkin service that enables the botmaster to upload and execute shell commands on all infected iPhone bot clients. Bots are programmed to send requests to Lithuanian C&C server with 5 minute intervals to get the new control commands (scripts for iPhone shell) allowing bot to grow more clever and appeal to the other servers around the world.
Ikee.B Code Research
To find out how viruse's code looks like and its reverse engineering two methods of analysis were used - manual and automated analysis. IDA Pro was used for to analyze the two binary apps written for iPhone's ARM. A IDA Pro plugin called Desquirr was utilized to properly recognize the start and end of the functions compiled for ARM processor. As the basic version of decompiler wasn't enough to fulfill all the analysis purposes, its functionality was extended. Below is the image that describes the Ikee.b working scheme.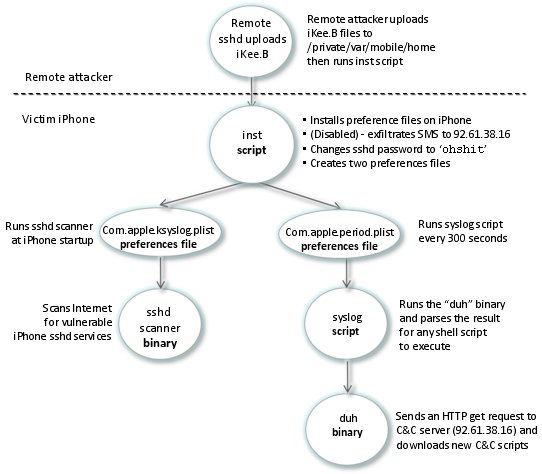 The process starts with a remote attacker (remotely infected iPhone) that detects a potential victim - other iPhone with active internet connection, SSH connection enabled and default password. Once such device is detected, attacker connects to the victim remotely and extracts the install files to directory
The process starts with a remote attacker (remotely infected iPhone) that detects a potential victim - other iPhone with active internet connection, SSH connection enabled and default password. Once such device is detected, attacker connects to the victim remotely and extracts the install files to directory
/private/var/mobile/homeThat's it, Ikee.b is now ready to be installed. The installation process is performed with help of inst shell script that creates a Ikee directory on the infected device. The script also installs com.apple.ksyslog.plist and com.apple.period preference files. It also can archive all the SMS messages from the iPhone and send them to servers in Lithuania, but this function was disabled for internet version of the virus. It changes the default root password as well.
Ikee.B Propagation and Botnet Control Logic
The propagation of Ikee.B is implemented this way: the virus scans specific Internet IP addresses for SSH services (port 22/TCP), and performs attempts to connect to services that respond as root, using the password 'alpine'. The Ikee.B's scanning and infection logic can be found in a binary application named sshd, which is configured to RunAtLoad, with KeepAliveenabled, via the com.apple.ksyslog preference file. As soon as the vulnerable iPhone with SSH enabled is found, sshd will upload a copy and unpack of iKee.b's a package consisting of 6 files to the victim's iPhone. After that it runs the inst script. Ikee.B's clients are programmed to communicated with dedicated botnet server which IP address is 92.61.38.16. Ikee.b connects there to allow the bot master to send new script logic to infected iPhones. The script can be customized for specific bot client depending on individual client ID. Botnet installation script installs with the com.apple.period.plist preferences. The file programs the infected device to run the syslog shell script once in 5 minutes. For more info check the SRI INTERNATIONAL AnalysisiKee.B / iKee.d Sourcecode Download:
By following the link below you can download the source codes of both Ikee.b and Ikee.d viruses. The only reason we have uploaded those archives for - is to give you the opportunity to protect your phones by digging into the worm's code and understanding how it maintains. Please note that the archive is password protected. Contact me on Google+ to get the password. Download (only for educational and security purposes) If you feel or know that your iPhone is infected with evil Ikee.b worm - check this article to find out how to delete it.Recent Blog

Ultimate Guide: How to turn Off Restricted Mode on iPhone?

Automate Apple GSX check result obtaining?

iRemove Unlock iPhone 5S, 5C, 5, SE, 4S/4 Software

MacOS High Sierra Features: Set Up Websites in Safari on Mac
How to Enable iOS 11 Mail Reply Notification on iPhone 7

How to Bypass Apple Watch Passcode Problem
LetsUnlock Services List
iPhone & iPad Activation Lock Bypass
Use LetsUnlock iCloud Tool to bypass Activation Lock Screen on iPhone and iPad running on iOS version up to 14.6.
Read More
Unlock Passcode Disabled iPhone or iPad
LetsUnlock iCloud Tool is ready to remove Find My and unlock your passcode disable device running on iOS 13.x.x in one click!
Read More
MacOS iCloud Activation Lock Bypass
The LetsUnlock Mac iCloud Activation Lock Bypass Tool will help you to remove Activation Lock on an iCloud locked Mac which is stuck on Activation Lock Screen with no need to enter the correct Apple ID and password.
Read More
Mac EFI Firmware Passcode Bypass
The LetsUnlock EFI Bypass Tool is a one button solution, which you click to start the EFI Unlock process. Bypass EFI with out password! Everything else does the software.
Read More
MacOS iCloud System PIN Bypass
The LetsUnlock MacOS iCloud System PIN Bypass Tool was designed to bypass iCloud PIN lock on macOS without passcode!
Read More