The NCK code actually looks like this:
NO=123456789012345&It has 15 unique numbers (which also can have different meanings and sign the locktype). Simple bruteforce will take years but if you have those parameters it will take significantly less time to generate the whole code. NCK codes are used in all mobile phones but Apple iPhone has the most strongest "NCK" protection.
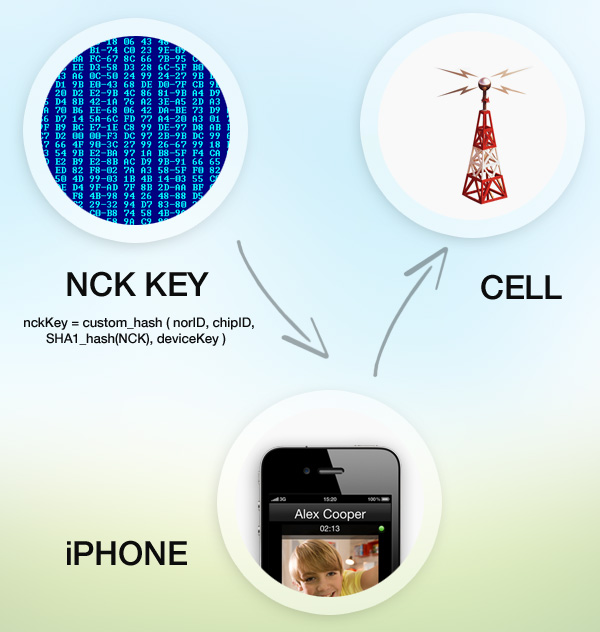
NCK generation algorithm:
In pseudo code, it looks like thisdeviceKey = SHA1_hash(norID+chipID) nckKey = custom_hash(norID, chipID, SHA1_hash(NCK), deviceKey) rawSignature = generateSignature(SHA1_hash(norID+chipID), SHA1_hash(chipID)) Signature = RSA_encrypt(rawSignature, privateRSAkey) encryptedSignature = TEA_encrypt_cbc(Signature, nckKey)So now you can use this algorithm to find exploits to unlock iPhone. I know that it can take a lot of time but there is a real possibility to find the way out. Also I tried to describe you the NCK key signing and verification process in general below. The NOR ID is the hardware chip id burned into the baseband chip of the device. It is actually burned into the chip and the size is 64 bytes for iPhone 3G and 128 bytes for the iPhone 3GS. CHIP IP is the motherboard id.
Baseband NCK key signing and verification process:
The encryptedSignature is then saved to a protected memory area - the device has been locked. This happens when Apple issues the AT+CLCK="PN",1,"NCK" command presumably directly after manufacturing the phone. When testing a network code key, the baseband firmware reads the encryptedSignature, calculates the deviceKey and the nckKey from the entered NCK, decrypts the encryptedSignature with the nckKey using TEA, decrypts it once more with the public RSA key and verifies the signature with the SHA1 hashes of the chipID / norID. Here's the pseudo code from Dogbert hacker:deviceKey = SHA1_hash(norID+chipID) nckKey = custom_hash(norID, chipID, SHA1_hash(NCK), deviceKey) encryptedSignature = readEncryptedSignature() Signature = TEA_decrypt_cbc(encryptedSignature, nckKey) rawSignature = RSA_decrypt(Signature, publicRSAKey) if ( (rawSignature has correct format) and (rawSignature contains both SHA1_hash(norID+chipID), SHA1_hash(chipID)) and (Lock status byte in rawSignature is OK) ) .. accept every SIM card else .. block non-authorized SIMsA correct NCK key can be stored the application processor part of device. When a certain flag is set, the application firmware (iOS) feeds the NCK into the baseband modem during the boot-up. If the decrypted rawSignature passes the check, the baseband unlocks.
Bruteforcing the NCK from the SecZone
So as you know the NCK code is stored in iPhone baseband memory in the zone which is called SecZone. So the first thing is needed to be done is dumping your NOR memory. When done decrypt it using TEA algorithm (Dogbert's perl script). There is the algorithm that is used to generate that code. Geohots NCKBF program could do around 100,000 keys/second which would produce a hit in many years, or complete a search in 317 years. But those who don’t know, the Dev Team members have found the NCK to be only of 40 Bits (5 digits) which can theoretically be cracked with a brute force attack. Big thanks to Dogbert for providing the clearest info on Apple's NCK algorithm.Recent Blog

Ultimate Guide: How to turn Off Restricted Mode on iPhone?

Automate Apple GSX check result obtaining?

iRemove Unlock iPhone 5S, 5C, 5, SE, 4S/4 Software

MacOS High Sierra Features: Set Up Websites in Safari on Mac
How to Enable iOS 11 Mail Reply Notification on iPhone 7

How to Bypass Apple Watch Passcode Problem
LetsUnlock Services List
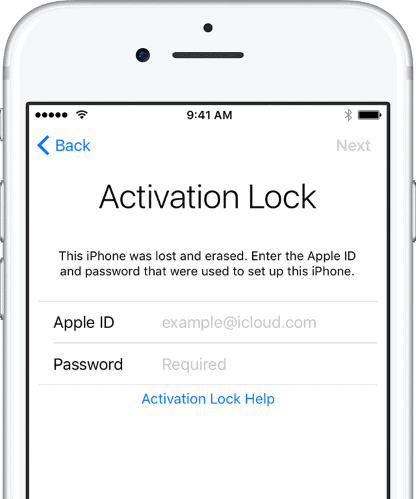
iPhone & iPad Activation Lock Bypass
Use LetsUnlock iCloud Tool to bypass Activation Lock Screen on iPhone and iPad running on iOS version up to 14.6.
Read More
Unlock Passcode Disabled iPhone or iPad
LetsUnlock iCloud Tool is ready to remove Find My and unlock your passcode disable device running on iOS 13.x.x in one click!
Read More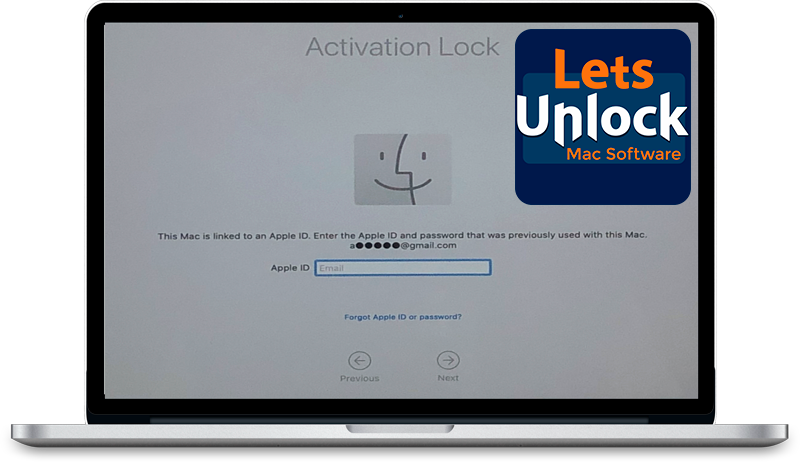
MacOS iCloud Activation Lock Bypass
The LetsUnlock Mac iCloud Activation Lock Bypass Tool will help you to remove Activation Lock on an iCloud locked Mac which is stuck on Activation Lock Screen with no need to enter the correct Apple ID and password.
Read More
Mac EFI Firmware Passcode Bypass
The LetsUnlock EFI Bypass Tool is a one button solution, which you click to start the EFI Unlock process. Bypass EFI with out password! Everything else does the software.
Read More
MacOS iCloud System PIN Bypass
The LetsUnlock MacOS iCloud System PIN Bypass Tool was designed to bypass iCloud PIN lock on macOS without passcode!
Read More