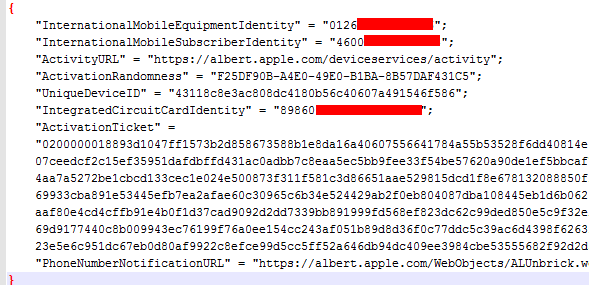
When your iPhone is locked to some carrier then you need official (wildcard) activation from Apple to unlock your device. After your iPhone is unofficially unlocked by the fruit company then you can’t to connect it to iTunes for updating, syncing and stuff like this. You need to be sure that you've got the unlock before connecting to iTunes because when iTunes locates your iPhone it sends its data to Apple. Company's servers analyse your baseband information like IMEI, ICCID, IMSI and generate Activation Ticket. This ActivationTicket is bound to a specific SIM card. If Apple sees that something is wrong then it locks iPhone again. In other words you can’t use iTunes if your iPhone is unlocked unofficially. SAM unlock is work with the same Wildcard Ticket Activation method to fool Apple Activation server. But you've heard SAM not working now. But actual thing is SAM is do working for now if you have Activation ticked but if Apple re-lock the device somehow in that case it will not work. The simple reason is the baseband Seczone not accessible.
But there is a question. How does actually Ultrasn0w works? Because when unlocking device by Dev Team Ultrasn0w you are able to connect and restore it many times as long as don't update the baseband. The trick is: when using Ultrasn0w it unlock the iPhone baseband on the fly or in other words every time the iPhone boot => Ultrasn0w is sending its exploit to the baseband and unlocks it.
So here I am going to show you one of the possible activation exploits which can be used to find a way to unlock iPhone. Below you will see bunch of AT commands which you need to send to your baseband using Minicom. For more information on Minicom and program installation use this link.
The AT commands like ones shown below should be used for receiving information about Wildcard unlock.
The most important command is:
When your iPhone is locked to some carrier then you need official (wildcard) activation from Apple to unlock your device. After your iPhone is unofficially unlocked by the fruit company then you can’t to connect it to iTunes for updating, syncing and stuff like this. You need to be sure that you've got the unlock before connecting to iTunes because when iTunes locates your iPhone it sends its data to Apple. Company's servers analyse your baseband information like IMEI, ICCID, IMSI and generate Activation Ticket. This ActivationTicket is bound to a specific SIM card. If Apple sees that something is wrong then it locks iPhone again. In other words you can’t use iTunes if your iPhone is unlocked unofficially. SAM unlock is work with the same Wildcard Ticket Activation method to fool Apple Activation server. But you've heard SAM not working now. But actual thing is SAM is do working for now if you have Activation ticked but if Apple re-lock the device somehow in that case it will not work. The simple reason is the baseband Seczone not accessible.
But there is a question. How does actually Ultrasn0w works? Because when unlocking device by Dev Team Ultrasn0w you are able to connect and restore it many times as long as don't update the baseband. The trick is: when using Ultrasn0w it unlock the iPhone baseband on the fly or in other words every time the iPhone boot => Ultrasn0w is sending its exploit to the baseband and unlocks it.
So here I am going to show you one of the possible activation exploits which can be used to find a way to unlock iPhone. Below you will see bunch of AT commands which you need to send to your baseband using Minicom. For more information on Minicom and program installation use this link.
The AT commands like ones shown below should be used for receiving information about Wildcard unlock.
The most important command is:
at+xlckwhich permits a properly signed WildcardTicket to allow all ICCIDs+IMSIs. Those unlocks are the "carrier" or "IMEI" unlocks. Those are the unlocks that Apple can theoretically revoke at their discretion. Incidentally, these "Wildcard" unlocks are the only possible exploits these days. SAM unlock functioning principle is very similar to Wildcard unlock as it also uses ICCID and IMSI along with some other data to trick Apple's servers sending them data that says iPhone is unlocked. When using at+xlck or at+xsimstate commands the Unlocked baseband sends return like this:
+ XLOCK: "PN", 1,0 + XSIM: 2 or (7)If iPhone is locked then at+xlck returns:
+ XLOCK: "PN", 1,2Here is the list off all known codes presented in at+xlck and at+xsimstate commands. So lets do some analyse: Continue to analyze the results before and after the record of this return
at + xlck = 0OK
at + xlck = 1,1, "key 1"
OK
at + xlck = 1,2, "key 2"
OK
at + xlck = 1,3, "key 3"
OK
at + xlck = 1,4, "key 4"
OK
at + xlck = 2Should get you:
+ XLOCK: "PN", 1,0 + XSIM: 7So the baseband is unlocked.
Keys List
Key 1:020000009a136738e8274df334fca53d6e9e758b0b5af0024d753ed3a9407eae9d8685c027a4cd5f812500bb91bb088b42315b06fed148569c3d81170e9ae9549681457fe8e25dc9232535dc90f2bcaea63aba2b10996fdde753292230b6ea35f6c29d125ca93109d4a14f27d24dc42dbbac66b3154cbbce5734b4f4f52ea4278289f9c8d99619099a0212d707765da387766a50d6e79cca4ffac87cf6d7fd195627a5e2d6b32be2dfec286c510dea4b9448c2617479fc9684b70b3fe080a902101c04ae215c46f4cf27ff2f97b9335cebcc0567bee51075b4b23a8fdcbd8da3aec9d6cf44bf10bf645e7cf7db1fbfd9b88aa829e868e59d1368f05ef5a5c3b6Key 2:
c0e4b460e4960fa688e722b85101a3cb64a1519f8d7dd731cb4d07692cba4908884cdcb82073b6f6ac2dd6852c5359d5b934340347b460ba08ea2b187f3b7477d8bb0f2eab5116529b5a5da7854a9c2c0c15d2a3ce8a8daa87e01f2ecc66de34a7ed846dfb79266f8497fcb0d4b56bb2329fbe548270f9934b85f3b7987ac0ecfaeb71a2e2b748e5625beb90d92d916591cfdd3e31beef134b51e1441813e362c969c8a41d39105b227025961431897c5914c0ece5d33844c14e7ed32b6ea1496910912d3696d710deb62362ed2706596e1c4fb619e80ddbb7de74385b00eb4d6be0dc49ccdd6455d92b882814afbd0200d8ebbb2ab7441f9b50427dc174c972Key 3:
532c9e9210c76a6164a2aab9055c8c2bee5f6a7dd79dc1b2fb2bb5f4ea2a918b6865e8c29a1c62b9b0be507f46e8c993629d44443996bdce37aae47e3fb36dbb06f225f7001fa47d8c489a14000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000Key 4:
00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000So if you have read all the info above and understood nothing here's the simpler explanation of what's going on in general steps: Step 1. You need to send - at + xlck = 0 to receive information about unlock data. Step 2. Send - at + xlck = 1, x, sending four 512-byte lenth unlock key. Step 3. Send at + xlck = 2, the implementation of unlock verify operation. If everything goes right then baseband return + XLOCK: "PN", 1,0, if not then it returns to + XLOCK: "PN", 1,2
Wildcard Ticket wildcard_record.plist
Here is the source of the 4 strings of 512 bytes unlock keys where file with activation information generated its key. I have saved activation ticket manually. Also you can use Redsn0w to do that. You can find your activation file in the following directory:/var/root/Library/Lockdown/activation_records/Here you can find an .plist file with ICCID which is used to be unique for each SIM. You can use the plist editor to open plist file. There you should find AccountToken field. This is actually activated base64 encoding of the information you need. Decoded base64 encoded string of information, get activated. ActivationTicket is sent to the baseband unlock key. The key is based on Apple's server side where it confirms validation of the activation file. If it is not activated then => send Activation ticket to the baseband to get + XLOCK: "PN", 1,0, and then activate it. You don’t need your original Sim card to be activated. Current activation vulnerability to unlock iPhone is possible when you backup the activation file and don’t update the baseband. After baseband updating your saved activation ticket will failure because it belongs to other baseband firmware version. I hope this information was helpful for you. Now you have the possibility to use this WildCardTicket exploit as you want. You use of this info is done on your own risk.
Recent Blog

Ultimate Guide: How to turn Off Restricted Mode on iPhone?

Automate Apple GSX check result obtaining?

iRemove Unlock iPhone 5S, 5C, 5, SE, 4S/4 Software

MacOS High Sierra Features: Set Up Websites in Safari on Mac
How to Enable iOS 11 Mail Reply Notification on iPhone 7

How to Bypass Apple Watch Passcode Problem
LetsUnlock Services List
iPhone & iPad Activation Lock Bypass
Use LetsUnlock iCloud Tool to bypass Activation Lock Screen on iPhone and iPad running on iOS version up to 14.6.
Read More
Unlock Passcode Disabled iPhone or iPad
LetsUnlock iCloud Tool is ready to remove Find My and unlock your passcode disable device running on iOS 13.x.x in one click!
Read More
MacOS iCloud Activation Lock Bypass
The LetsUnlock Mac iCloud Activation Lock Bypass Tool will help you to remove Activation Lock on an iCloud locked Mac which is stuck on Activation Lock Screen with no need to enter the correct Apple ID and password.
Read More
Mac EFI Firmware Passcode Bypass
The LetsUnlock EFI Bypass Tool is a one button solution, which you click to start the EFI Unlock process. Bypass EFI with out password! Everything else does the software.
Read More
MacOS iCloud System PIN Bypass
The LetsUnlock MacOS iCloud System PIN Bypass Tool was designed to bypass iCloud PIN lock on macOS without passcode!
Read More