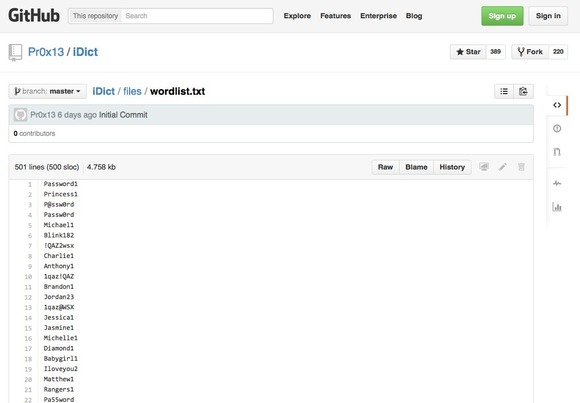
 Let's learn the anatomy of an hack tool attack and how protect iCloud account.
iDict and similar remote brute-force attacks rely on three elements: a way to perform excessive tests of passwords for an individual account; a way to bypass an account protection and a weak password.
The users with the strong password that are used only to current account should not worry about brute force attacks. If you pick a weak password, brute force method allow attacker to capture, encrypt passwords and test it with home-computer equipment against billions of passwords only per second. In this case, finding one password match helps the attacker to find all accounts that use the same password. So in order to protect personal iCloud documents you need to create strong password with 15 to 20 characters or mix of letters, numbers, and punctuation.
Let's learn the anatomy of an hack tool attack and how protect iCloud account.
iDict and similar remote brute-force attacks rely on three elements: a way to perform excessive tests of passwords for an individual account; a way to bypass an account protection and a weak password.
The users with the strong password that are used only to current account should not worry about brute force attacks. If you pick a weak password, brute force method allow attacker to capture, encrypt passwords and test it with home-computer equipment against billions of passwords only per second. In this case, finding one password match helps the attacker to find all accounts that use the same password. So in order to protect personal iCloud documents you need to create strong password with 15 to 20 characters or mix of letters, numbers, and punctuation.
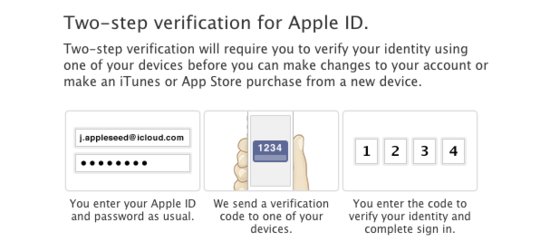 iDict came with a list of a few hundred default passwords that meet Apple’s minimum requirements for an Apple ID. These could be added to any person that use the code. Making these short lists even more dangerous, it’s possible for hackers to chain attacks.
Two-step verification is real way to protect iCloud password against attacks. If you’re using any password on about list, or anything similar, you need to change it immediately. Or better please enable two-step verification. The other two elements required for an iDict attack to work. Although this process again is under the control of Apple. The company should pay a real attention on its problem.
iDict came with a list of a few hundred default passwords that meet Apple’s minimum requirements for an Apple ID. These could be added to any person that use the code. Making these short lists even more dangerous, it’s possible for hackers to chain attacks.
Two-step verification is real way to protect iCloud password against attacks. If you’re using any password on about list, or anything similar, you need to change it immediately. Or better please enable two-step verification. The other two elements required for an iDict attack to work. Although this process again is under the control of Apple. The company should pay a real attention on its problem. Recent Blog

Ultimate Guide: How to turn Off Restricted Mode on iPhone?

Automate Apple GSX check result obtaining?

iRemove Unlock iPhone 5S, 5C, 5, SE, 4S/4 Software

MacOS High Sierra Features: Set Up Websites in Safari on Mac
How to Enable iOS 11 Mail Reply Notification on iPhone 7

How to Bypass Apple Watch Passcode Problem
LetsUnlock Services List
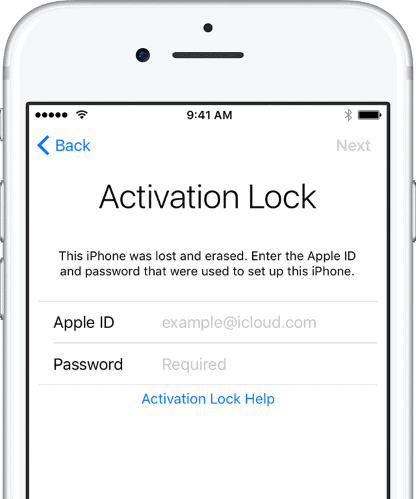
iPhone & iPad Activation Lock Bypass
Use LetsUnlock iCloud Tool to bypass Activation Lock Screen on iPhone and iPad running on iOS version up to 14.6.
Read More
Unlock Passcode Disabled iPhone or iPad
LetsUnlock iCloud Tool is ready to remove Find My and unlock your passcode disable device running on iOS 13.x.x in one click!
Read More
MacOS iCloud Activation Lock Bypass
The LetsUnlock Mac iCloud Activation Lock Bypass Tool will help you to remove Activation Lock on an iCloud locked Mac which is stuck on Activation Lock Screen with no need to enter the correct Apple ID and password.
Read More
Mac EFI Firmware Passcode Bypass
The LetsUnlock EFI Bypass Tool is a one button solution, which you click to start the EFI Unlock process. Bypass EFI with out password! Everything else does the software.
Read More
MacOS iCloud System PIN Bypass
The LetsUnlock MacOS iCloud System PIN Bypass Tool was designed to bypass iCloud PIN lock on macOS without passcode!
Read More